Cyber incident response plan
This Plan details how Intellischool will respond in the event of a cyber security incident.
This document is an adaptation of the Australian Cyber Security Centre's best practice document, and is a redacted version of Intellischool's internal full policy and plan. It has been provided online as a reference for potential clients undertaking a due diligence process; if there is a specific requirement or question that this version does not answer, please get in touch with our team. We'll provide more information where required provided it does not represent an over-exposure of internal processes.
➡️ Purpose
To support a swift and effective response to cyber incidents aligned with Intellischool’s security and business objectives.
➡️ Objectives
- To provide guidance on the steps required to respond to cyber incidents.
- To outline the roles, responsibilities, accountabilities and authorities of personnel and teams required to manage responses to cyber incidents.
- To outline legal and regulatory compliance requirements for cyber incidents.
- To outline internal and external communication processes when responding to cyber incidents.
- To provide guidance on post-incident activities to support continuous improvement.
➡️ High-level incident response process
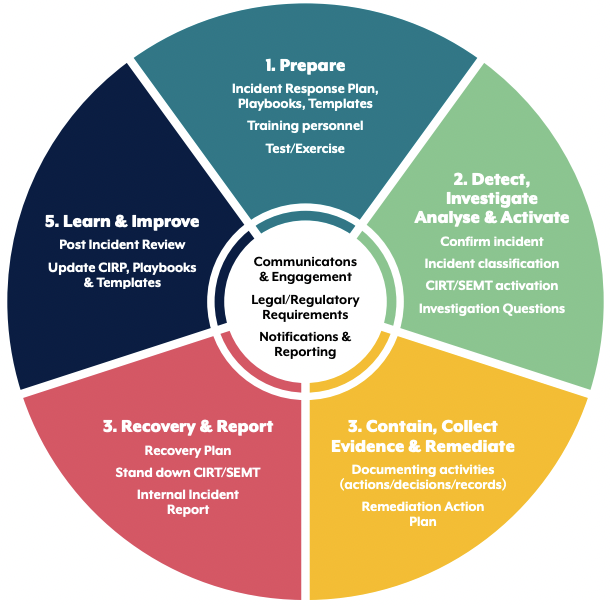
➡️ Common security incidents and responses
Common threat vectors
| External/removable media | An attack executed from removable media or a peripheral device (e.g. malicious code spreading onto a system from an infected USB flash drive). Note that by default, Intellischool-owned devices do not allow the use of removable media. |
| Attrition | An attack that employs brute force methods to compromise, degrade, or destroy systems, networks, or services (e.g. a DDoS intended to impair or deny access to a service or application or a brute force attack against an authentication mechanism, such as passwords). |
| Web | An attack executed from a website or web-based application (e.g. a cross-site scripting attack used to steal credentials or a redirect to a site that exploits a browser vulnerability and installs malware). |
| An attack executed via an email message or attachment (e.g. exploit code disguised as an attached document or a link to a malicious website in the body of an email). | |
| Impersonation | An attack involving replacement of something benign with something malicious (e.g. spoofing, man in the middle attacks, rogue wireless access points, and SQL injection attacks all involve impersonation). |
| Improper usage | Any incident resulting from violation of an organisation’s acceptable usage policies by an authorised user, excluding the above categories (e.g. a user installs file sharing software, leading to the loss of sensitive data). |
| Loss or theft of equipment | The loss or theft of a computing device or media used by an organisation (e.g. a laptop, smartphone or authentication token). |
Common cyber incidents
| Type/Description | Response |
| Denial of Service (DoS) and Distributed Denial of Service (DDoS): overwhelming a service with traffic, sometimes impacting availability. |
As per Intellischool's internal threat mitigation policy, immediately contact CloudFlare to enhance attack protection services. Escalate to the CIRT immediately and notify customers of any potential downtime. All Intellischool services exposed to the Internet are done so through Cloudflare to minimise the risk of a successful DoS or DDoS attack. |
| Phishing: deceptive messaging designed to elicit users’ sensitive information (such as banking logins or business login credentials) or used to execute malicious code to enable remote access. |
If identified by staff through successful malicious content SOC to take action as appropriate as per Intellischool's threat mitigation policy, including blocking the sender's domain and/or IP address from future interaction with Intellischool e-mail or web services. |
| Ransomware: a tool used to lock or encrypt victims’ files until a ransom is paid. | All Intellischool files/systems that could be affected by ransomware are secured and backed up daily (if not more frequently). Escalate to the CIRT, remediate the access vector that allowed the ransomware to be installed in the first place, and immediately restore the most recent backup. |
| Malware: a Trojan, virus, worm, or any other malicious software that can harm a computer system or network. |
Immediately identify and isolate any affected systems or devices from the Intellischool network, and remediate as appropriate (which may include factory resetting the device in question and restoring backed-up data). All Intellischool user devices are segregated from production systems to reduce the chance of user device to prod system infection. |
| Data breach: unauthorised access and disclosure of information. |
Ascertain the scope of the breach and immediately notify the primary contact of any potentially affected customer. Provide guidance to the customer on communication with the school community/ies. Ascertain the attack vector used to gain access to the data and remove any access points. Notify the relevant government authorities as required. |
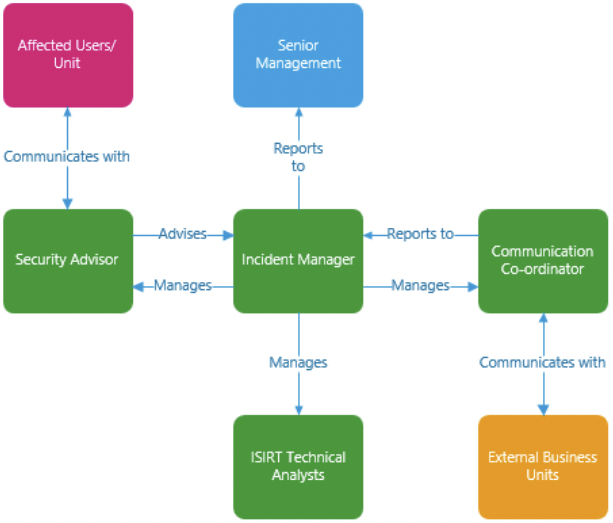
➡️ Roles and responsibilities
Points of contact for reporting cyber incidents
| Name | Hours | Contact details | Responsibilities |
| Engagement team | 0800-1700, Mon-Fri, AEDT | +61 3 9068 6444 help@intellischool.co |
First Point of Contact |
| Head of Engineering | 0800-1700, Mon-Fri, AEDT | +61 3 9068 6444 | Technical Contact |
Cyber Incident Response Team (CIRT)
| Job title | Contact details | Role title | Responsibilities |
| Chief Technical Officer | +61 3 9068 6444 | Incident Manager |
|
| Head of Engineering | +61 3 9068 6444 | Deputy Incident Manager |
|
| Legal Counsel | +61 3 8007 2208 | Security Advisor |
|
| Engineering Team | +61 3 9068 6444 | Incident Responder |
|
| Engagement Team | +61 3 9068 6444 | Comms Coordinator |
|
Senior Executive Management Team (SEMT)
Significant cyber incidents may require the formation of the SEMT to provide strategic oversight, direction and support to the CIRT, with a focus on:
- Strategic issues identification and management
- Stakeholder engagement and communications (including Board and ministerial liaison, if applicable)
- Resource and capability demand (including urgent logistics or finance requirements, and human resources considerations during response effort).
| Name | Contact details | Title | SEMT Role |
| Dave Philp | +61 3 9068 6444 | Chief Executive Officer | SEMT Chair |
| Joshua Turci | +61 3 9068 6444 | Chief Technology Officer | SEMT Deputy Chair |
| Scott Barnsley | +61 3 9068 6444 | Head of Engineering | SEMT Deputy |
| Rowan Freeman | +61 3 9068 6444 | Head of Product | |
| Andrew Nicholls | +61 3 9068 6444 | Head of Commercial | |
| Yehuda Orelowitz | +61 3 9068 6444 | Legal Counsel |
➡️ Roles and relationships
➡️ Communications
Internal communications
Upon activation of this CIRP, all Intellischool employees are to be notified immediately via Slack.
[Redacted]
External communications
Employees will be provided with a standard response to any enquiries and must direct further enquiries to the Comms Coordinator in the CIRT.
[Redacted]
Where Intellischool identifies that a customer has been affected by a breach or incident, that customer shall be notified immediately via e-mail and a telephone call to the primary contact by a member of the CIRT. Intellischool will support the customer's primary contact in the distribution of information to school communities (if required).
If definitive information is not forthcoming within 4 hours of activating this plan, all possibly affected customers will be notified via e-mail. Updates will continue via e-mail every 4 hours until the scope of the incident has been identified, at which point communications shall be more targeted (as appropriate).
Intellischool will not broadcast about the activation of this plan via social media of any kind.
➡️ Incident notification and reporting
In addition to the affected customers, the following entities will be notified in the event of a Cyber Security Incident:
| Incident type/ threshold | Organisation/ agency | Contact details | Key requirements | Personnel responsible |
| Ransomware | Australian Cyber Security Centre | 1300 CYBER1 | Available here | Security Advisor |
| Data breach (Notifiable) |
Office of the Australian Information Commissioner | Available here | Available here | Security Advisor |
[Redacted]
➡️ Detection, investigation, analysis and activation
Incidents can be detected in several ways, including, but not limited to:
- Self-detected incidents (e.g. Intrusion Detection and Prevention systems);
- Notifications received from service providers or vendors; and
- Notifications received from trusted third parties such as the ACSC.
Incident classification
| Classification | Description |
| Critical |
|
| High |
|
| Medium |
|
| Low |
|
➡️ Activation
This Cyber Incident Response Plan will be activated in any event of a self-detected incident or validated notification from a third party.
➡️ Investigation
The CIRT will attempt to answer the following questions during an initial investigative process:
- What was the initial intrusion vector?
- What post-exploitation activity occurred? Have accounts been compromised? What level of privilege?
- Does the actor have persistence on the network or device?
- Is lateral movement suspected or known? Where has the actor laterally moved to and how?
- How is the actor maintaining command and control?
- Has data been accessed or exfiltrated and, if so, what kind of data?
Depending on the answers to these questions, further specific investigative actions may take place as defined by Intellischool's internal policies.
➡️ Containment, evidence collection and remediation
[Intellischool's detailed containment and remediation plans have been removed from the public version of this document, as they speak to specifics about Intellischool's internal systems and architecture.]
Where relevant, Intellischool will involve the relevant authorities (including Victoria Police, the Australian Federal Police, and/or other government agencies) to ascertain exactly what evidence should be collected. Specialist consultants will be brought in in the event that Intellischool staff are not capable of collecting evidence as required; any specialists accessing sensitive data will be required to meet the same background checking requirements as Intellischool employees.
➡️ Recovery [redacted]
Intellischool's recovery plan has been removed from the public version of this document, as it speaks to specifics about Intellischool's internal systems and architecture.
➡️ Learn and improve
A Post Incident Review (PIR) is to be conducted after Intellischool has experienced a cyber security incident. It shall include a hot debrief, held immediately after networks and systems have been recovered, and a formal debrief to be held after the incident report has been completed (but no more than two weeks after the incident).
The PIR shall cover, at an absolute minimum, four key points:
- What were the root causes of the incident and any incident response issues?
- Could the incident have been prevented? How?
- What worked well in the response to the incident?
- How can our response be improved for future incidents?
[Redacted]
Following the PIR, this Cyber Incident Response Plan may be updated and will be tested appropriately. Additionally, any training for employees recommended in the PIA shall be enacted within 3 months of the PIA being published (except where training is unavailable during the 3 month period, in which case it should be conducted as early as possible).
[Redacted]
➡️ Document control
| Author | Dave Philp |
| Owner | Josh Turci |
| Date created | January 16 2021 |
| Last reviewed | March 2025, Dave Philp |
| Endorsement | May 7 2021, Dave Philp and Josh Turci |
| Next review | July 2025 |